Action1 Block USB Devices is a cloud-based software that allows users to quickly discover endpoints and detect the usage of USB devices, SD cards, and other removable media across their entire network of workstations. The software provides immediate visibility into the devices being used and their location.
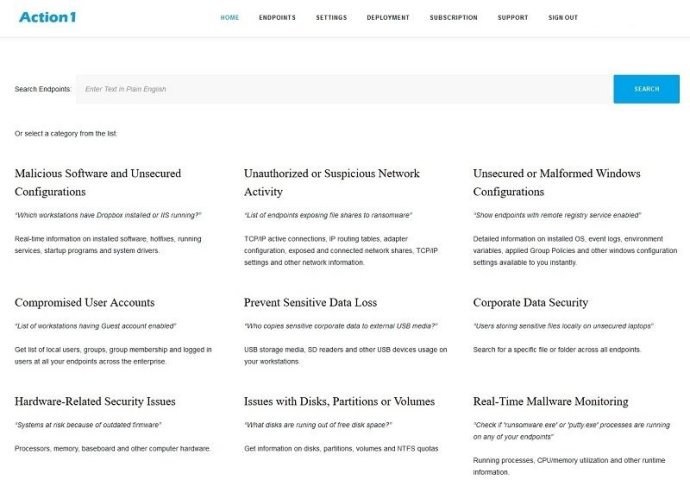
One of the advantages of Action1 Block USB Devices is that it works on the cloud, through which it discovers every endpoint in seconds. This means you can query every workstation in your network, enabling you to see the USB devices, SD cards, and other removable media being used and their locations. The endpoint security platform assists IT departments to keep their endpoints secure and protect corporate data.
Besides, the Action1 Endpoint Security Platform is a completely SaaS platform that operates via an online web interface without needing any form of installation of management tools. The basic functionality comes at no cost, making it cost-effective. With the software running in the cloud, Action1 discovers every endpoint in seconds, offering plain English queries for their entire network.
Furthermore, the software is capable of providing an up-to-date list of endpoints and ensuring their security. It offers information on the workstations that have Dropbox installed, IIS running, or which ones are exposing file shares to ransomware. Additionally, it shows endpoints with a remote registry service enabled list of workstations having a guest account enabled.
Moreover, it lets you know who is copying sensitive corporate data to external USB media, check if ransomware.exe or putty.exe are running on any of your endpoints, identify users that store sensitive files locally on unsecured laptops, and finally, determine the system at risk because of outdated firmware.
In summary, Action1 Block USB Devices is undoubtedly a powerful software platform that guarantees endpoint security and keeps the corporate data safe continuously. The software's sophisticated functionalities and cloud-based operations are a game-changer, giving IT departments peace of mind that their endpoints are secure.
Version 2.6:
- Ability to search endpoints using plain English queries
- Extensive set of predefined queries covering many aspects of endpoint security
- Seamless installation
- Custom queries