This software enables users to discover vulnerable websites using DORKS, and then extract and analyze all the data stored in the corresponding MySQL database.
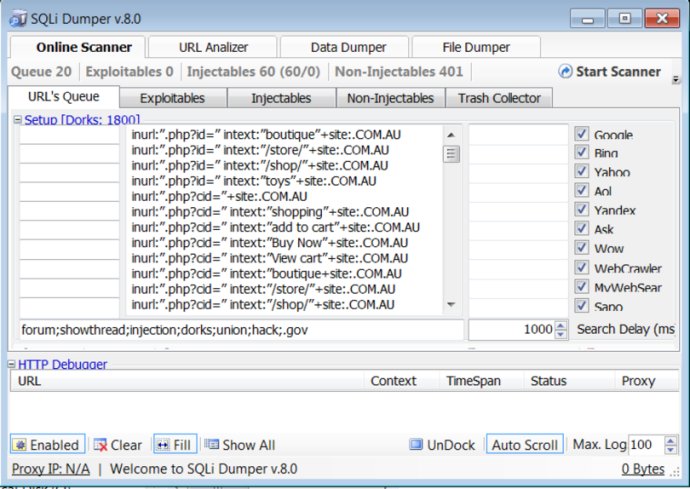
Although SQL injection is primarily known as an attack vector for websites, it's a technique that can be used to attack any kind of SQL database. SQL injection attacks let attackers spoof identity and tamper with existing data. These attacks can cause issues with repudiation such as voiding transactions or changing balances. With SQL injection, it's possible to completely disclose all data on the system, destroy it, or render it otherwise unavailable. In some cases, attackers can even become administrators of the database server.
Overall, SQLI is a powerful software tool that provides comprehensive access to vulnerable web sites with inadequate security measures in place. Its capability to penetrate data-driven applications makes it an essential tool for software security professionals and developers looking to protect their websites and data from malicious attacks.
Version 8: N/A