This software allows users to monitor and control access to the registry, preventing unauthorized changes or access. It also provides the ability to create virtual registry keys or values through modified registry calls.
The configuration manager is responsible for implementing the registry and allows registry filtering drivers to receive notifications of each registry operation before it processes the operation. This is possible through a set of REG_XXX_KEY_INFORMATION data structures, which contain information about each registry operation. By registering a RegistryCallback routine in the registry filter driver, the software can receive these notifications and even block certain registry operations.
To be notified of registry operations, the software must register the RegistryCallback routine with REG_NOTIFY_CLASS, which specifies the type of registry operation that the configuration manager is passing to the routine. The configuration manager then calls a driver's RegistryCallback routine and passes a REG_NOTIFY_CLASS enumeration value to the routine. The RegistryCallback routine can inspect the contents of input and output buffers that are supplied for registry operations.
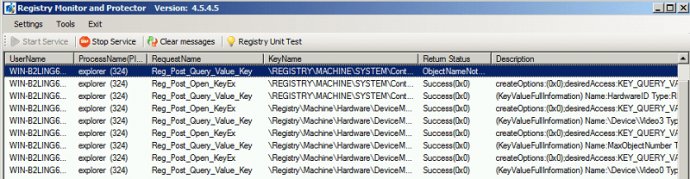
One of the key features of this software is its ability to track registry changes by monitoring registry calls. To do this, the software must register notification classes such as 'Reg_Post_Create_Key', 'Reg_Post_Delete_Key', and 'Reg_Post_Set_Value_Key'. When the registry key, value or security was modified, the callback routine will be invoked with a data structure that contains this information.
Overall, I found the Registry Monitor and Protector software to be a valuable tool for any Windows user who wants to protect their registry and track changes to it. Its ability to filter registry calls, receive notifications, and block certain operations makes it an ideal addition to any antivirus software package.
Version 5.1.8.1: Monitoring registry calls to track the registry changes, Blocking registry calls to prevent your registry from being changed by unauthorized processes, Modifying registry calls to create virtual registry key or value.