CPM II is a dedicated software that offers file and folder encryption capabilities for local, network, server, and external data storage.
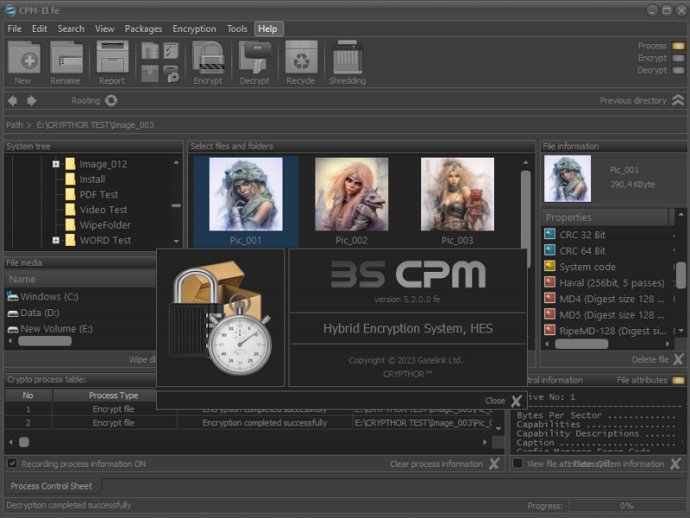
CPM II offers a range of useful features, including the ability to encrypt or decrypt selected files and folders, secure file packages, encrypt files within packages, decrypt files within packages, perform file integrity checks, control file modifications, and check the current status of files and directories.
The encryption process for files in packages, which have available meta-information and physical accessibility, is performed using session crypto mechanisms. These mechanisms utilize a set of proven cryptographic primitives, with the configuration being done automatically.
It's worth noting that all operations on files and folders saved in the package can only be performed when they are physically accessible. If there are any issues with accessing the files or folders, such as deletion or physical inaccessibility of a network drive, these problems will be recorded in the packet along with the time they were encountered.
CPM II finds its application in the protection of large arrays of files stored on various media. Implementing such protection can be complex and challenging, but the use of file packages automates the process, enhances service efficiency, and significantly improves the security of corporate solutions.
Often, the importance of storing, editing, transferring, and destroying files is overlooked by both users and those responsible for security. However, statistics show that threats related to unauthorized access by individuals are closely linked to these activities. With CPM II, it is possible to address these problems effectively through a highly secure cryptosystem that utilizes secure file packages.
One of the key advantages of CPM II is its utilization of highly effective standard digital data encrypting algorithms commonly used by government organizations and corporate structures. This ensures robust security for encrypted files and guarantees the protection of sensitive information.
Version 2.5.0.0:
File crypto manager;
Encrypt selected files and folders;
Create virtual disks;
Standard protection mode (SPM);
Package protection mode (PPM);
File integrity monitoring (FIM) functions;
Intuitive interface etc.