This software generates cryptographic hash values for single files and folders to verify file integrity, using popular algorithms like MD5, SHA-1, SHA256, SHA384, and SHA512.
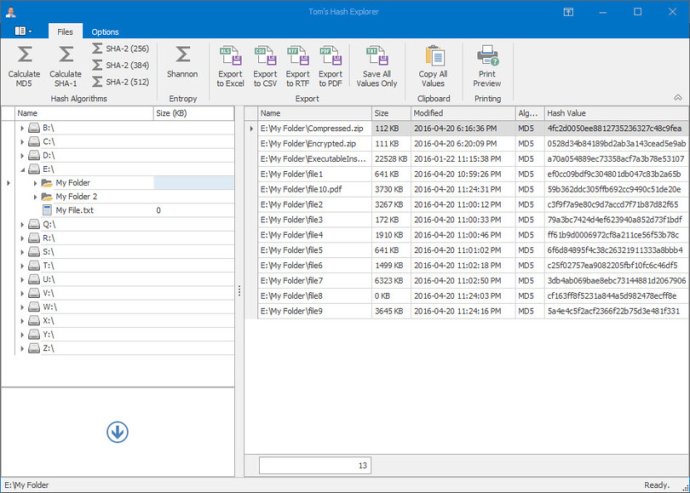
One of the key features is its ability to support the most popular hashing algorithms such as MD5, SHA-1, SHA256, SHA384, and SHA512. The Explorer-like user interface is also customizable, allowing users to choose from different themes/skins.
The multi-threaded computation engine is another standout feature, as it allows calculations to be performed rapidly and without any lag. Another feature is the ability to calculate file entropy using the Shannon's Entropy algorithm.
Users can also drag and drop files or folders for ease of use. Additionally, Tom's Hash Explorer can export full results to Excel, CSV, RTF, PDF, and other industry standard formats, print full results, and save hash values to a text file or copy to clipboard for easy import into whitelisting applications.
Overall, Tom's Hash Explorer is an excellent utility that aids in verifying file integrity for single files or to aid in file integrity investigations. Its easy-to-use interface and advanced features make it a must-have for anyone who requires fast and accurate cryptographic hash calculations.
Version 1.2: File Integrity Verification/Batch Verification