Action1 Running Process Explorer helps you identify running processes across your Windows network. It provides information such as process start time, file name, and command line for each process running on your networked computers.
Users can quickly obtain useful information about processes, including details like the process start time, executable file name, command line, and much more. Essentially, it offers users a central way view to the processes running on hundreds or thousands of systems simultaneously. This is especially useful for organizations looking to spot certain processes, such as unauthorized programs or ransomware, that might be running on their network.
Action1 Running Process Explorer is a part of Action1 Endpoint Security Platform, a cloud-based software that is entirely SaaS-based. With no management tools to install, users can access the platform via an online web interface. Also, its basic functionality is free to use.
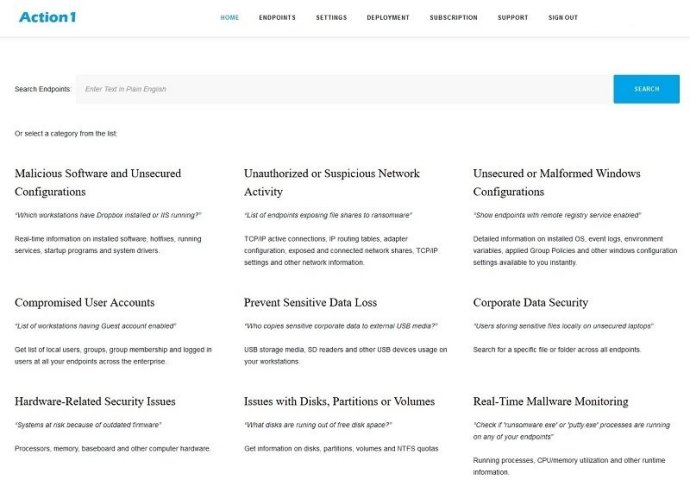
By running in the cloud, Action1 can discover all endpoints connected to an organization's network in just seconds. With its easy-to-use plain English query language, Action1 Endpoint Security Platform provides IT professionals with real-time information about an organization's endpoints. With it, IT departments can keep their endpoints secure and corporate data safe by knowing:
- What workstations have Dropbox installed or IIS running?
- Which endpoints exposing file shares to ransomware?
- What are the endpoints with remote registry service enabled?
- What workstations have Guest account enabled?
- Who copies sensitive corporate data to external USB media?
- Check if 'ransomware.exe' or 'putty.exe' processes are running on any of your endpoints.
- What users are storing sensitive files locally on unsecured laptops?
- What systems are at risk due to outdated firmware?
In conclusion, Action1 Running Process Explorer offers users a central way to quickly gather information on the processes running on their organization's endpoints. With Action1 Endpoint Security Platform's real-time information, IT departments can keep their endpoints secure and reduce the risk of running unauthorized software or exposing sensitive data.
Version 2.6:
- Ability to search endpoints using plain English queries
- Extensive set of predefined queries covering many aspects of endpoint security
- Seamless installation
- Custom queries