This utility offers cryptographic hash generation and verification in MD5, SHA-1, and SHA-256. It helps protect data integrity and prevent malicious modifications.
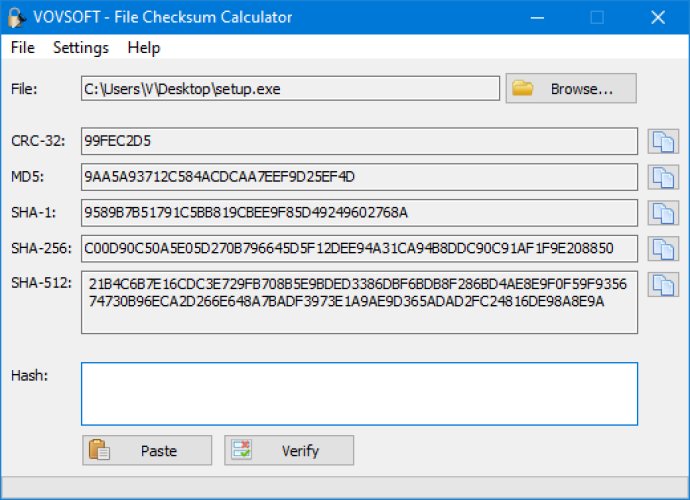
The most widely used cryptographic hash functions are the Secure Hash Algorithm (SHA) and Message Digest Algorithm-5 (MD5). This utility comes fully equipped with checksum functions that are used to validate the integrity of the generated hashes. There are two types of checksum utilities; one that calculates checksum values and the other that validates them by comparing them against a list of values. The second type is more effective and the only way to ensure data integrity.
Overall, this utility is an excellent addition to any cybersecurity toolkit as it ensures that your data remains protected against malicious attacks.
Version 1.2: Implemented multi-threaded calculation, faster now.